Let's talk about Cybersecurity.

TLDR; The rest of this page is well worth reading but it is very long!
We're cybersecurity experts specialising in securing businesses across New Zealand and Australia.
If you need help with:
- Assessing your current cybersecurity posture
- Hardening your systems using the ACSC Essential 8 framework
We can make that happen. Click the button below to get in touch and arrange a call.
Before we start, some quick cyber stats
The Australian Signals Directorate is Australia's Cyber Intelligence organisation and each year, they release a report. Here's some stats from the ASD Cyber Threat Report 2022-2023:
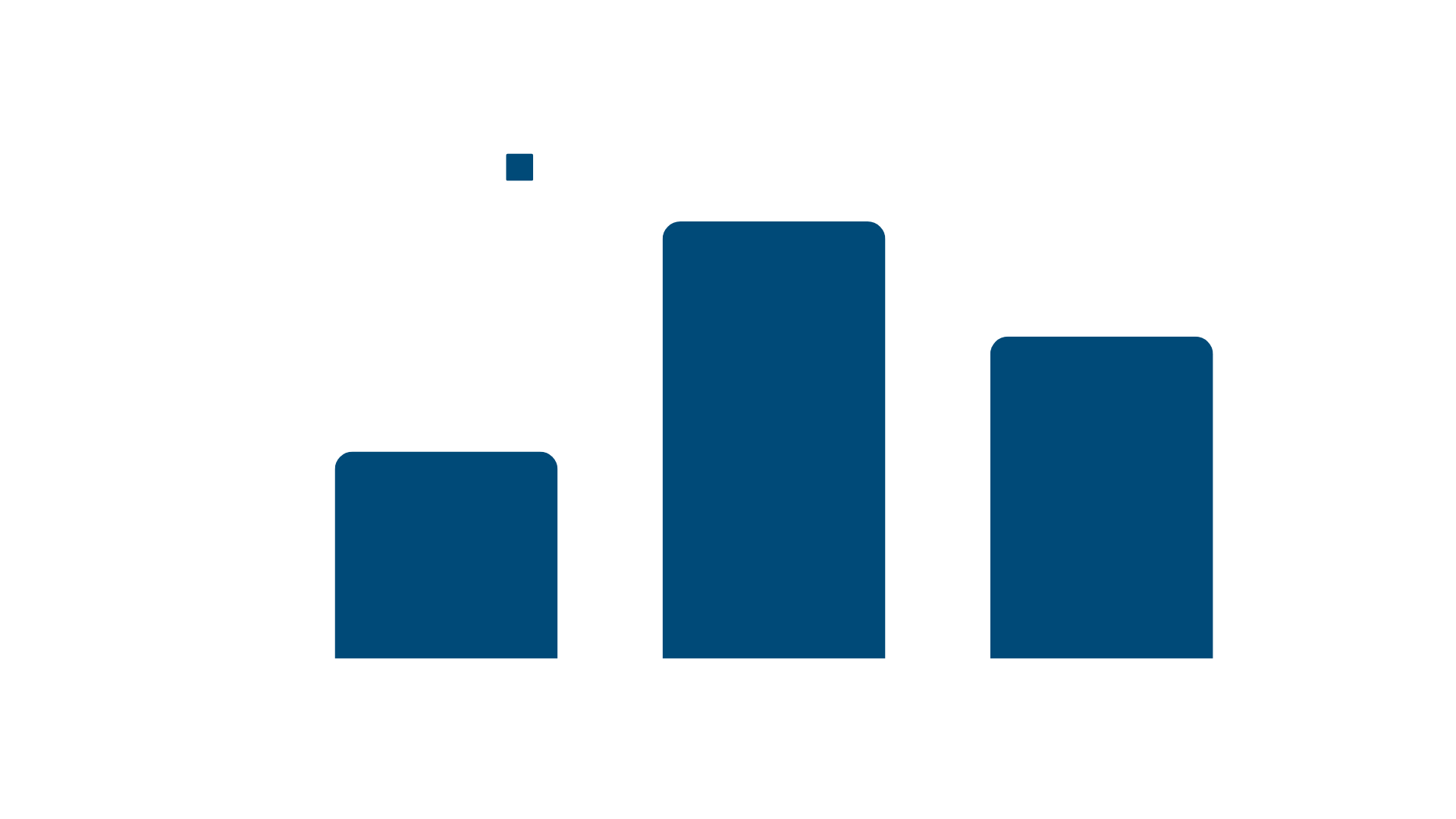
- The average cost of a cybercrime incident
- Small business: AUD$46,000
- Medium business: AUD$97,200
- Large business: AUD$71,600.
- In Australia there are nearly 94,000 cybercrime reports per year.
- We have no reason to believe New Zealand is any different. They can get us down here too!
As you can see, cybercrime is commonplace nowadays and we suspect that these figures are much lower than the actual rates as many businesses do not report incidents.
However, I'm sure you already know of a business or someone who has personally been affected and the disruption it caused both in their ability to operate but also the reputational aspect too.
Ok, we need to be secure, but what is "enough" security without spending too much?
It's almost like the ACSC was thinking about us here at 80with20 when they created the Essential 8 framework.
The ACSC recognised that:
A small number of proactive security measures could prevent a large percentage of cyber incidents.
By identifying these eight key preventative measures, they effectively applied the 80/20 rule to cybersecurity:
Implementing just 20% of possible security measures to mitigate 80% of potential threats.
Is Cybersecurity a cost or an investment?
We fully recognise that for most businesses, cybersecurity is a cost rather than a money maker. That's why we really like the Essential 8 program. You don't need to be the world's most cyber secure fish 'n' chips shop, but you do need to achieve an appropriate level of security these days.
It's basically as if the ACSC was saying:
"If you do nothing else, at least do the Essential 8 and you'll likely be ok".
We wholeheartedly believe that implementing the Essential 8 is affordable enough to be a viable investment in the long term protection of your business.
How can a hardened security posture actually make me money?
On the flip side, increasingly we see businesses requiring that their vendors, partners and even customers can demonstrate that they operate securely.
There have been plenty of instances recently where cyber security incidents have occurred due to an insecure interaction with a "trusted" vendor/partner.
Whilst we can help you become secure, we can also help you demonstrate your security practices by developing documentation that you can provide to your clients, vendors, and partners to show them where you stand on the matter.
This can help you win more work by distinguishing yourself from insecure competitors and increasing the trust they have in operating with you.
Our services
We offer two levels of service.
Level 1: Essential 8 Assessment
A comprehensive audit of your current cybersecurity posture, delivered as a detailed report.
Expand this for the full details - What We Look At
When we conduct an assessment, we're not just doing a one-time health check as a snapshot in time. Our goal is to identify possible tools/processes you could implement to ensure you remain secure going forward.
Here's what we're looking at:
- Application Patches: We check if you have a system in place to consistently keep your software up-to-date. It's not just about being current now, but staying current over time.
- Operating System Updates: We evaluate your processes for ensuring your computers' core systems are regularly updated.
- Multi-Factor Authentication: We assess your ongoing practices for using more than just passwords to log in. We're checking if this extra security is consistently applied across your systems and is enforced going forward for new users etc.
- Admin Privileges: We examine your protocols for managing who has the 'keys to the kingdom' in your systems and how these privileges are monitored and protected over time.
- Application Control: We evaluate your systems for controlling which programs can run, who can run them and where. We're looking for a persistent "bouncer" that's always on duty ready to boot out troublemakers.
- Microsoft Office Macros: We check your policies and systems for managing those little automated scripts in Office, ensuring they can't be exploited by attackers now or in the future.
- User Application Hardening: We look at how your web browsers and other common apps are set up to resist attacks, and how these settings are maintained over time.
- Backups: We examine your backup systems and processes to ensure you're not just saving copies of your important data, but doing so regularly, securely, and in a way that guarantees recoverability.
After this assessment, we provide a detailed report card showing where your ongoing processes are strong and where they need improvement.
Level 2: Essential 8 Implementation Program
Sometimes at the end of an assessment, you may decide you need an extra set of hands to get stuck in and implement the recommendations we've outlined in the assessment report.
We've put together an 8-month program where we work alongside you, implementing the Essential 8 strategies during this time.
Expand this for the full details - What We Actually Do
If you choose our implementation service, we establish robust, ongoing systems and processes. Here's what we do over those 8 months:
- Patch Your Apps: We implement and fine-tune automated systems to continuously update your software, ensuring security holes are closed fast, now and in the future.
- Update Your Operating Systems: We set up processes to keep your computers and servers running the latest, most secure versions at all times, not just once.
- Set Up Multi-Factor Authentication: We implement a comprehensive, ongoing multi-factor authentication system, making it consistently harder for unauthorised access (whilst still making it easy for you to access your own systems!).
- Manage Admin Privileges: We establish ongoing controls and monitoring for administrative access, keeping the 'keys to the kingdom' safe over the long term.
- Implement Application Control: We set up and maintain systems that continuously control which programs can run, providing constant protection against unauthorised software finding it's way into your environment.
- Control Microsoft Office Macros: We implement persistent policies to manage potentially dangerous scripts, allowing only necessary ones and monitoring for any changes.
- Harden User Applications: We establish ongoing processes to maintain tight security settings on common apps like web browsers, ensuring they remain tough targets.
- Set Up Robust Backups: We implement a comprehensive, automated backup system, ensuring your data is continuously protected, secure, and recoverable when needed.
Throughout this process, we're not just implementing tech solutions - we're establishing sustainable practices. We train your team, create documentation, and set up monitoring systems to ensure these security measures remain effective long after we've finished our initial work.
Remember, we spread this work out over 8 months, tackling one area at a time. This approach allows us to build a comprehensive, lasting security posture while minimising disruption and spreading the cost over time. It also gives your team time to fully adopt each new practice before we move on to the next if need be.
By the end of our engagement, your business will not only be significantly more secure, but you'll have the systems and knowledge in place to maintain that security over the long haul. You'll have the peace of mind knowing you've taken solid, sustainable steps to protect against current and future cyber threats.
Why Choose Us?
- Everyone at 80with20 is a doer, not a manager.
- We're a small co-operative business of solo freelancers so you work directly with us. No middlemen, no corporate jargon.
- Simple, transparent pricing.
- Open and honest reporting of project progress.
Spread the costs over 8 months:
Depending on the complexity of your business, we will most likely complete our work long before the 8 month mark.
But we get it, you hate spending money on cyber.
So we're happy to let you pay it off over the course of 8 months, 1 month for each Essential 8 area.
Don't wait for a breach take action today
Book your Essential 8 Assessment today and take the first step towards bulletproof security.